If you are in the business of protecting networks, you certainly spend enormous amounts of time grepping through pages of network log files trying to track down the origins of any threat that hits your network. Maybe you have a "SIEM" that helps you by storing this information for a window of time, and letting you search it.
If you are lucky, you can find your Russian malware inside the inbox of your director of finance's secretary in the form of a beautiful Word 0day. But there are days that the odds are not with you, and there is no explanation - no way to find out how your network got infected. Let's add a little bit more complexity to our mental game and let's make the threat a sophisticated implant, something like INNUENDO.
It's time to think USB! And that is exactly what this new release of El Jefe want to give you. A clear and visual way to track down every USB device connected on every computer on your network.
A good way to understand your USB devices and their relationship is to open the USB Relationship Map on your El Jefe server:
 |
| USB Relationship Map |
Double clicking on the devices will give us interesting information about the type of device and who has plugged it in.
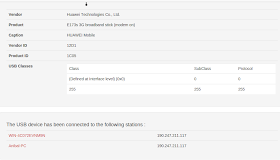 |
| This Huawei 3G Modem has been used on two workstations. Why are we even using Huawei modems?!? |
You can also obtain a list of every USB device plugged and unplugged from any given endpoint or all endpoints. This will give us a good idea of the HUAWEI mystery we want to highlight in this post.
 |
| This list of USB devices on the endpoints has beautiful Christmas colors. |
The Events view always provides us with a good picture of how this will correlate with process generation, and as expected it doesn't let us down. Seconds after connecting the 3G modem Autorun.exe was executed on the machine. This is not pretty at all.
 |
| Event view |
The Thai Antivirus BKav knows something that neither the Russian or the Estonian AV's know, WHAT IS THIS .exe HIDING?
 |
| BKav identifies the binary as a KeyLogger |
With one click in El Jefe we can now use Cuckoo to start to analyze the binary more, and even search our entire enterprise to see where else it has been installed. But we leave that as an exercise for the reader.
We hope you enjoy the El Jefe 2.2 release!
USB autorun.exe should not execute automatically on recent Windows. That will only work from optical media. Sounds like the victim was running Windows XP and deserved to get owned ;)
ReplyDelete