One of the great new features in ElJefe May release is the integration of the Cuckoo malware analysis system as part of our interface. Cuckoo runs the malware executable in a
sandboxed environment inside a virtual machine and produces amazing data, which we display in the El Jefe interface for you. However, configuring it is not a trivial task. That's why we put together a little blogpost to make our users happier. Always thinking about our El Jefe users, is our motto!
We are going to setup the host machine
and the guest machine. The last one is where we are going to run the
malicious files.
The following commands will install
the necessary files:
$ sudo apt-get install python python-sqlalchemy python-bson python-pip libcap2-bin $ sudo pip install sqlalchemy bson Django
You
also need to install mongodb. You can download the necessary files
from http://www.mongodb.org/downloads.
When Cuckoo is analyzing a submitted
files there are some modules and libraries we can install to get
better and more complete analysis and reports. These modules are
optional but their installation is highly recommended.
A list of the these packages can be found at: http://docs.cuckoosandbox.org/en/latest/installation/host/requirements/#installing-python-libraries
We are using setcap to give privileges
to tcpdump to run as root without having to run Cuckoo as root.
$ sudo setcap cap_net_raw,cap_net_admin=eip /usr/sbin/tcpdump
We can check the results with:
$ getcap /usr/sbin/tcpdump /usr/sbin/tcpdump = cap_net_admin,cap_net_raw+eip
You will need to create a new user, you can do that with the following command:
$ sudo adduser cuckoo
You can download Cuckoo from
http://www.cuckoosandbox.org/download.html. You will need to copy the Cuckoo folder into the El Jefe root folder.
You should see a directory listing like this:
client cuckoo dependencies
installer webapp
You will also need to uncomment some lines of code to make cuckoo work:
webapp/settings.py lines 105 to 124
webapp/xmlserver/ElJefeXmlServer.py
lines from 55 to 58.
webapp/home/views.py lines 44, 45,
1055, 1316 to 1334.
webapp/analysis/views.py
lines 20 to 25.
webapp/templates/base_.html remove
the {% comment %} and {% endcomment %} tags on lines 121 and 142.
Now it's time to setup the virtual
machine where we are going to run and analyze our binaries. Cuckoo
supports VirtualBox, KVM and VMWare for virtualization. We choose VMWare as our virtualization software, so the following steps will
show you how to configure Cuckoo to work with VMWare. If you wish to
use other virtualization software, follow the guidelines in the following URL: http://docs.cuckoosandbox.org/en/latest/installation/guest/.
First, we'll need to create a new virtual machine. The preferred OS is Windows XP, but you can use the OS of your preference. Obviously for future versions of El Jefe we will support automatically choosing the right target VM based on the El Jefe client's OS.
We need to install Python on the virtual machine and PIL (http://www.pythonware.com/products/pil/) if we want Cuckoo to be able to take screenshots of the binary as it runs.
Now it's time to configure the virtual machine's networking. We are going to disable the Windows Firewall first, and
then create a virtual host only network for the guest and the host.
We are going to use the 192.168.100.0 network, the guest configuration will be:
IP Address: 192.168.100.100
Netmask: 255.255.255.0
Gateway: 192.168.100.1
Cuckoo supports DNS resolution, so you
can use 192.168.100.1 as your DNS server. In our experience, we get
better analysis results by using a public DNS server.
And the host configuration (for the vmnet adapter) will be:
Ip Address: 192.168.100.1
Netmask: 255.255.255.0
You can choose whatever network and
addreses you like.
Now we need to configure packet forwarding on the host machine to give the guest machine Internet access. We can do this with the following commands ( replacing eth0 with your outgoing interface and vboxnet0 with your virtual interface).
iptables -A FORWARD -o eth0 -i vboxnet0 -s 192.168.56.0/24 -m conntrack --ctstate NEW -j ACCEPT iptables -A FORWARD -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT iptables -A POSTROUTING -t nat -j MASQUERADE sysctl -w net.ipv4.ip_forward=1
This concludes the networking setup. Now we need to install the
cuckoo agent on the guest, by copying agent.py, located in
cuckoo/agent in the El Jefe root folder, to the Windows Startup folder.
Now it's time to make a snapshot. Before executing a malware binary the snapshot is reverted and then the binary is executed and analyzed.
Next, we will see how to setup the
configuration files on Cuckoo.
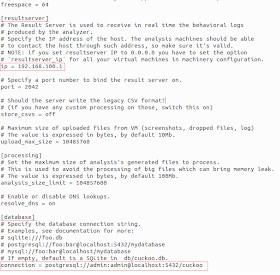
[cuckoo/conf/auxiliary.conf]
Change the interface to the one you are using.
[cuckoo/conf/cuckoo.conf]
Set your db connection on the
[database] section and the result server IP address on the
[resultserver] section (we are using
192.168.100.1).
[cuckoo/conf/reporting.conf]
Set the mongodb settings on the
[mongodb] section.
[cuckoo/conf/vmware.conf]
If you are going to use only one VM,
you will need to modify the stuff inside the [cuckoo1] section only,
otherwise you will have to create one additional section for every
extra VM you wish to use.
Inside these sections you will have to
set the VM path, snapshot name and IP address of the machine (we are
using 192.168.100.100).
We are done setting Cuckoo for El Jefe.
Before starting El Jefe remember to start the mongodb and postgresql
services. You will also need to start the cuckoo.py service from
cuckoo/cuckoo.py in the El Jefe root folder.
So in conclusion, you should now have Cuckoo set up for yourself, integrated into the world's most powerful open source host monitoring system, and ready for your incident response team to use. We welcome any comments or questions, and of course are ready to help you if you have problems.
David Arch




No comments:
Post a Comment